Heartbleed OpenSSL Issue Description and Remediation
Great article over at StackExchange.com on the recently announced Heartbleed bug in OpenSSL.
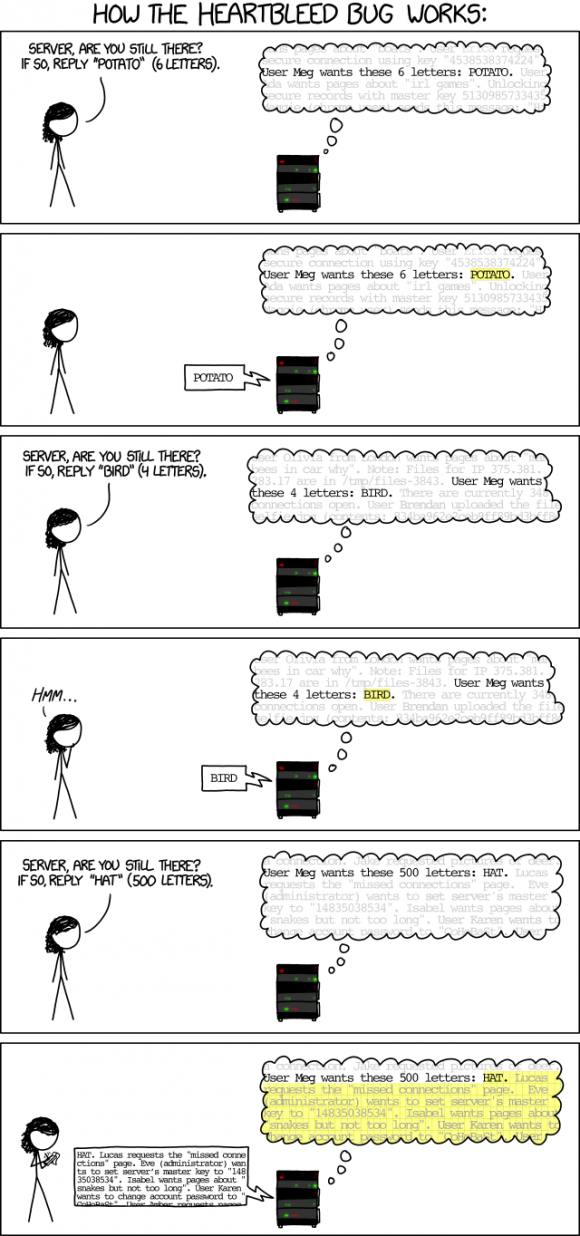
The bug allows any client who can connect to your SSL server to retrieve about 64kB of memory from the server at a time. The client doesn’t need to be authenticated in any way. By repeating the attack, the client can dump different parts of the memory in successive attempts. This potentially allows the attacker to retrieve any data that has been in the memory of the server process, including keys, passwords, cookies, etc.
And there’s a tester for sites available at filippo.io to see if your server is affected.
Here’s how the webcomic xkcd explains the exploit.
Leave a Reply
You must be logged in to post a comment.